WisQuas™ How-To
1. What is WisQuas?
The WisQuas engine attempts to reveal that which may be hidden, through slight fuzzing, enumeration, and fingerprinting around your entire domain and its web services (‘Digital Footprint Discovery and Inventory’). Using a small number of web requests, WisQuas attempts to identify areas of weakness around Information Disclosures, Security and Service Misconfigurations, Default Installations, Missing Input Sanitization, and more. Hidden web containers granting access to Shadow VHosts and localhost data, are detected along with WAF bypassing payloads, Host Header Manipulations, successful VERB Tampering, and User Agent redirection. DNS anomalies and Domain Shadowing may also be detected across a domain.
2. How to use WisQuas...
A. Sign-up & Logging In – Getting started with WisQuas
B. Scanning – Running WisQuas on your domain
C. Generating a Report – Identifying issues and investigating scores & stats
D. Viewing Results – Subdomain results explained
E. Searching – Domain vs. Global searching
F. OSINT and ‘Next Pivots’ – Digital Footprinting / Threat Intel
B. Scanning – Running WisQuas on your domain
C. Generating a Report – Identifying issues and investigating scores & stats
D. Viewing Results – Subdomain results explained
E. Searching – Domain vs. Global searching
F. OSINT and ‘Next Pivots’ – Digital Footprinting / Threat Intel
2A. Sign-up & Logging In - Getting started with WisQuas
A. Go to the URL and complete the Sign-up form. (By signing up you agree to the Terms of Use) https://wisquas.lostrabbitlabs.com/signup
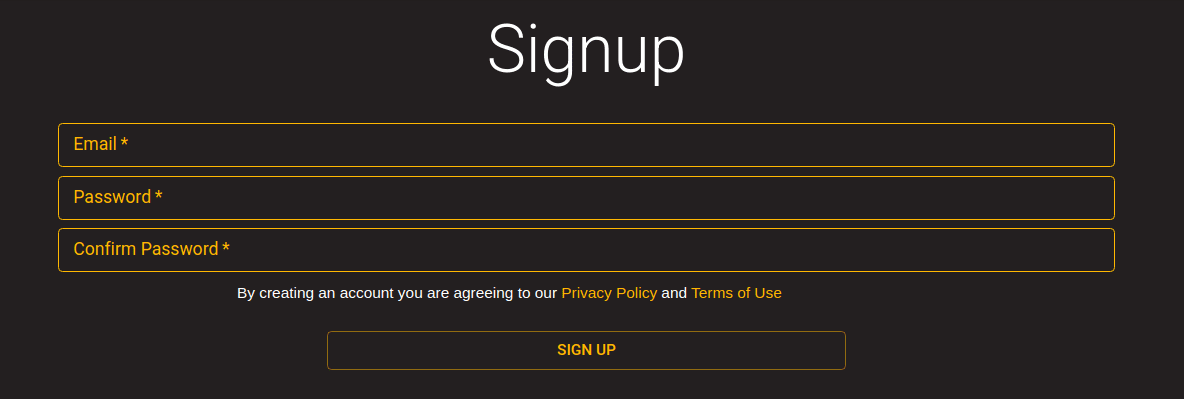
B. Once the signup process has been completed, you can log into your account using the link: https://wisquas.lostrabbitlabs.com/login
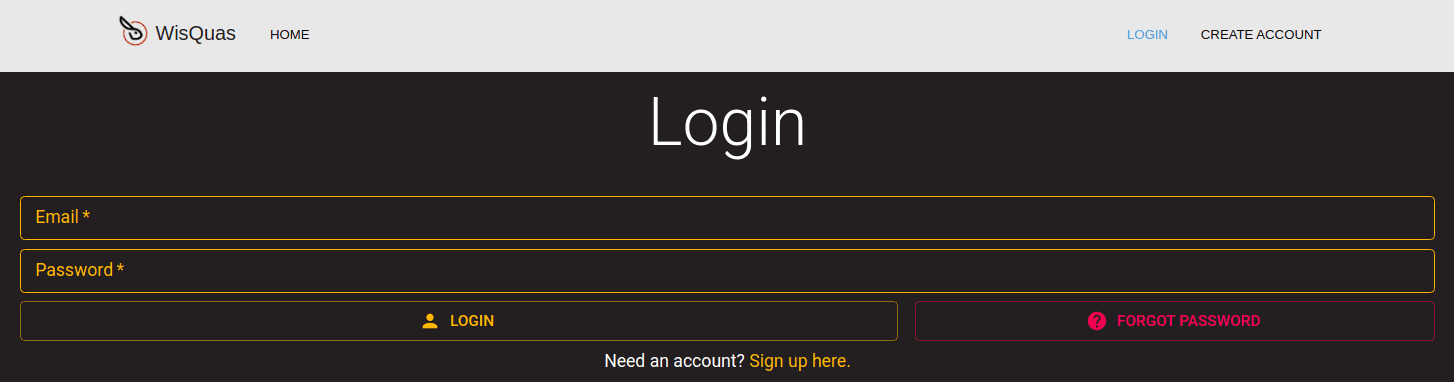
Account Types & Descriptions
Registered: Email sign-up required. Access to Shared Reports & On-Demand Scanning.
On-Demand: Registered account required. Adhoc scanning for your personal/business vulnerability & inventory scanning needs.
Business (Starts at $999/mo): 10 user accounts (includes admin account), 50 scan credits, API Access.
Enterprise (Custom Quote Required): Private On-Prem/Virtual solution with unlimited scanning, private workers and private database.
If you would like to purchase a WisQuas account, use the link below to find the license that works for your budget:
https://wisquas.lostrabbitlabs.com/pricing
https://wisquas.lostrabbitlabs.com/pricing
C. After successfully logging in, you will be presented with the main WisQuas dashboard:
2B. Scanning with WisQuas
A. Click on the 'scan' button or input the domain you want to scan into the 'target or rql' input bar (redirects to the scan page or processes RQL based on input) and click 'Next'. If you do not have a Business or Enterprise account type, the On-Demand option will be used. For this tutorial, we will assume the user is On-Demand.
B. Scan settings can be added and modified on Step 2 of a scan. By default, the scan setting will be set to PRIVATE SCAN, making it so that only your account can view the results of the scan. Switching this to 'OFF' will publicly tag the scan and allow any registered user the ability to view the results. Custom header key/value pairs can be added and are appended to every request. Default ports of 80/443 are used but if other web service ports are known before hand, they can be added here. Notification emails can be added for when after the report is complete, email updates can be sent out. Scans can be repeated for users based on the times they choose, but these will discontinue if the scan credits reach 0. The Extended Vuln Scan flag runs a set of curated Nuclei templates and has the ability to throttle. Additional Subdomains can be appended to the scan for added value in-case those records are hidden or are not found in public databases. Users also have the ability to have the scan stay in a 'defined' scope of targets.
C. Payload settings can be adjusted and customized to the user's needs. The more payload's the longer the scanning process. Our pre-defined lists are a good basis for most customer's needs. Different verbs, hosts, and user-agents can be appended and customized as well. Additional throttling can be used here for added cushion. This is a separate throttle than the throttling applied on the Extended Vuln Scan.
D. Confirmation of applied settings is the final step in the scanning process before payment with On-Demand. An estimated amount of subdomains will be calculated based on OSINT results and will be used as the basis for calculating costs of the scan. The cost of an On-Demand scan increments $25 for every 50 subdomainsfound during OSINT lookups or applied in the defined scope section. Any additional subdomains discovered during the scanning process through our own efforts and techniques will be free-of-charge.***Double check your scan settings before launching a scan because all submitted scans are final and non-refundable***
NOTE: Scanning a domain can take several hours depending on the amount of subdomains, firewalls/WAFs, speed and resiliency of services, and more. Be patient for all crawls to complete.
2C. Generating a Report - Identifying issues and investigating scores & stats
A. The Researcher,Business, and Enterprise paid accounts come with the ability to generate a domain-wide report that shows all unique titles, servers, cookies, redirect locations, IP addresses, and more. Simply type the desired name into the 'Generate Report' input bar and click the ‘View Report’ button.

B. After a brief moment your results should load, and you will be presented with the report:
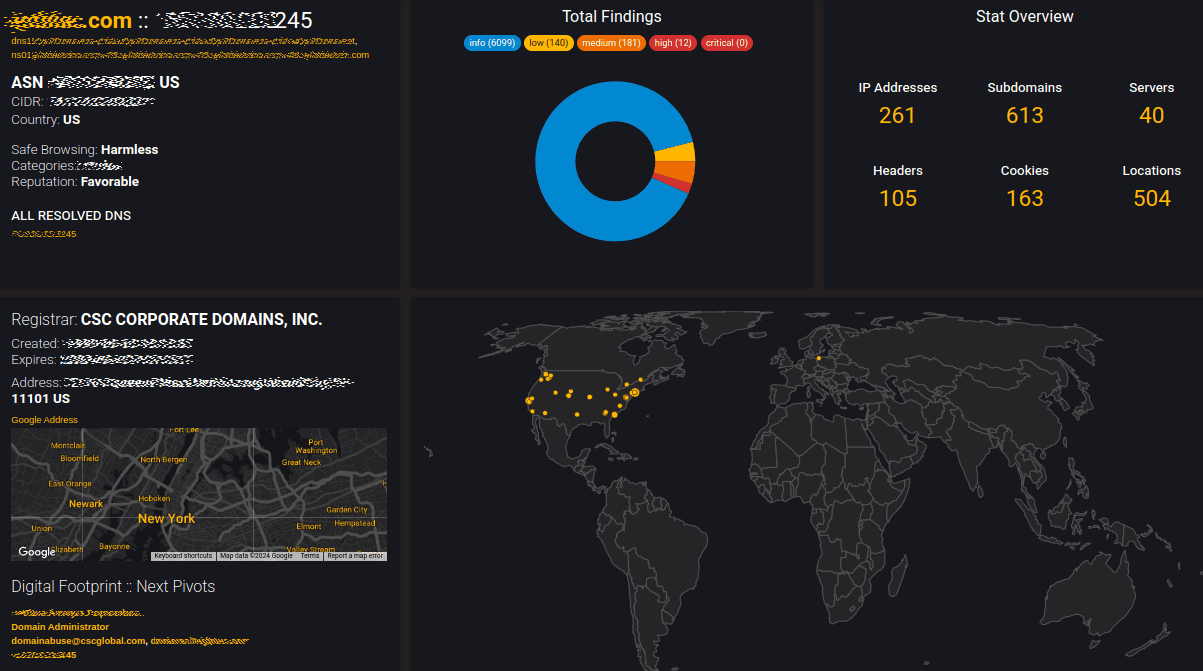
C. If all crawls have been completed for your domain scan, you will see the date and timestamp after the 'Completed' status (left-middle of view), otherwise you will see 'In Progress' and will need to wait for all results to complete to get the final report. From the status results below we can see that there were 88 total subdomains discovered (which can be copied to your clipboard by click the 'COPY SUBDOMAINS' button), of which 178 web services were observed.

D. Further explanation of each Report output section will be provided below. Many data-points within the WisQuas report view are clickable, and lead to additional resources (NOTE: some of these links are outside the WisQuas web service framework, use at your own discretion).
Domain & IP Address Info
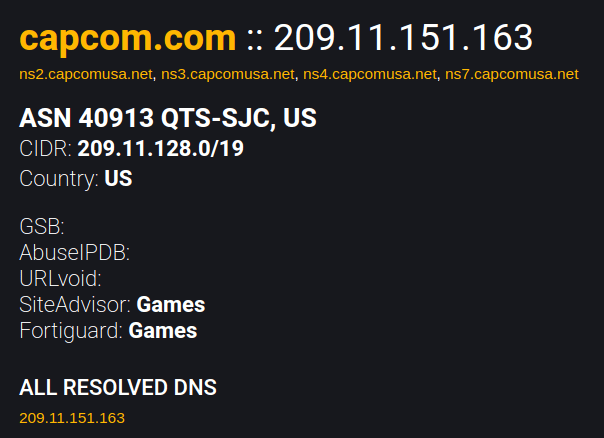
Domain & Scanned IP/Host
ASN / GEO Information
Reputation Lookups / Blocklists
All Resolved DNS (click on host for ASN Info)
ASN / GEO Information
Reputation Lookups / Blocklists
All Resolved DNS (click on host for ASN Info)
Registrant & Geo-Location Info
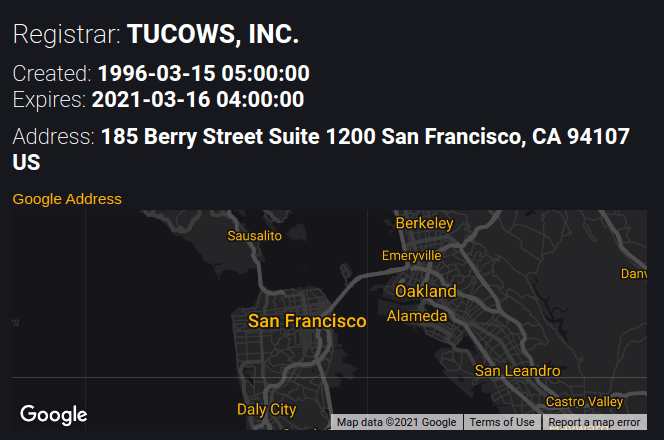
Registrar Info
Domain Creation & Expiration Dates
Company Address / Google Maps Link (click for more info)
Domain Creation & Expiration Dates
Company Address / Google Maps Link (click for more info)
Digital Footprint & Next Pivots
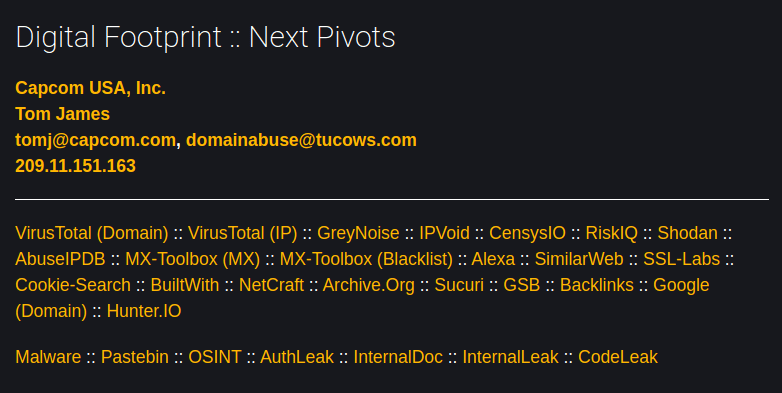
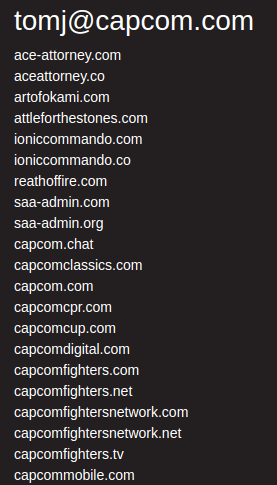
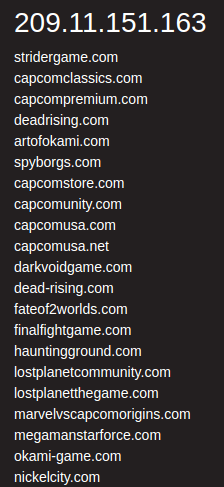
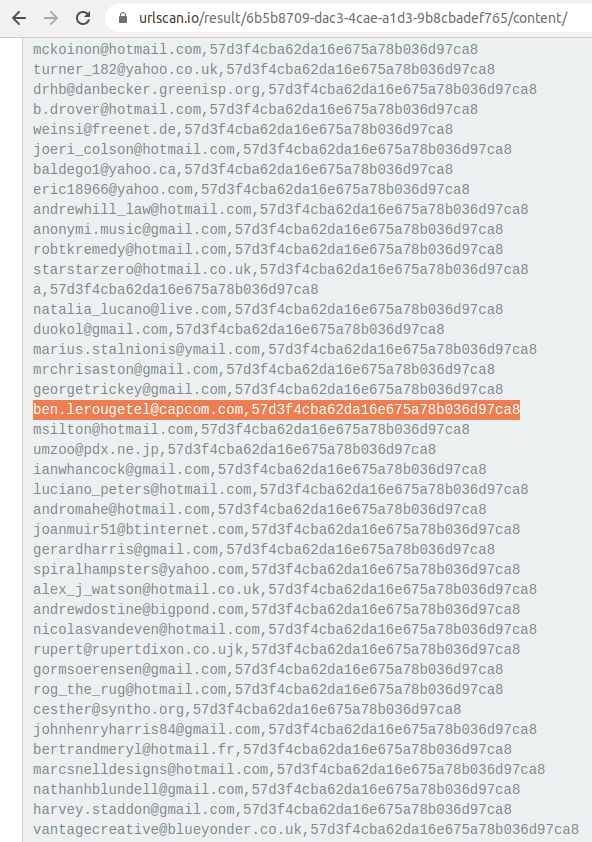
E. On some views you will be presented with Whois Information, Digital Footprint & Next Pivots, along with OSINT & informational links to external sites. Click on the ‘Next Pivots’, which include the Whois attributes (organization name, person, emails, IP address) and you will be shown a list of domains associated with that attribute.
'Findings of Interest' Section
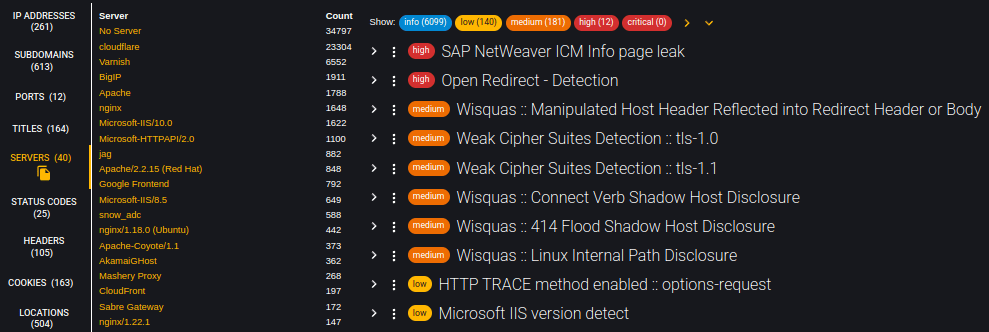
'Findings of Interest' Section
IP Addresses
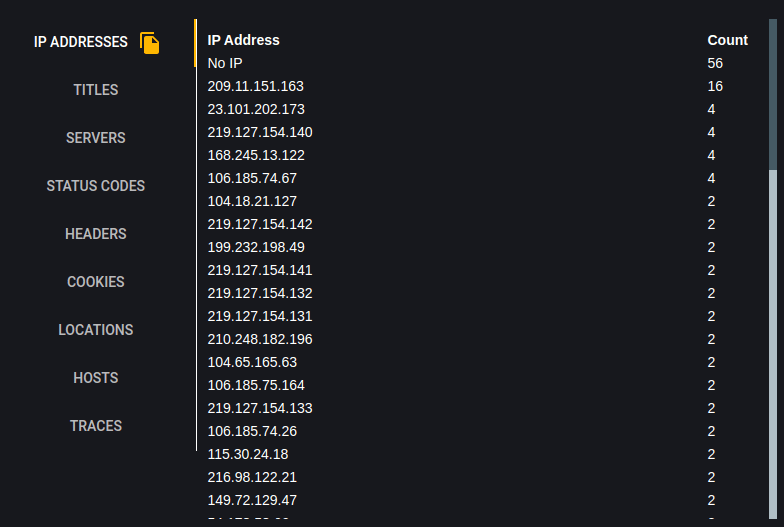
Titles
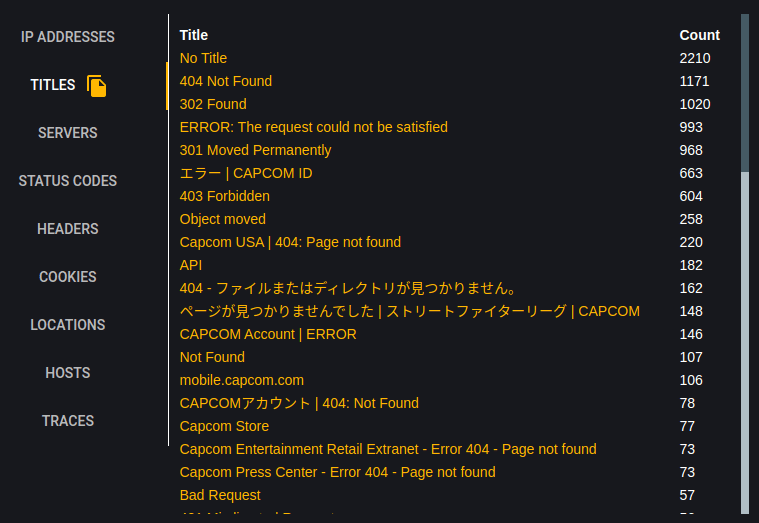
Servers
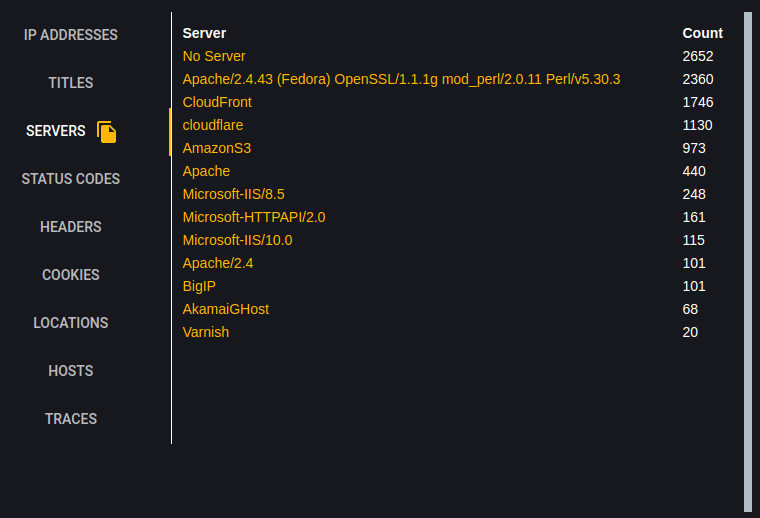
Status Codes
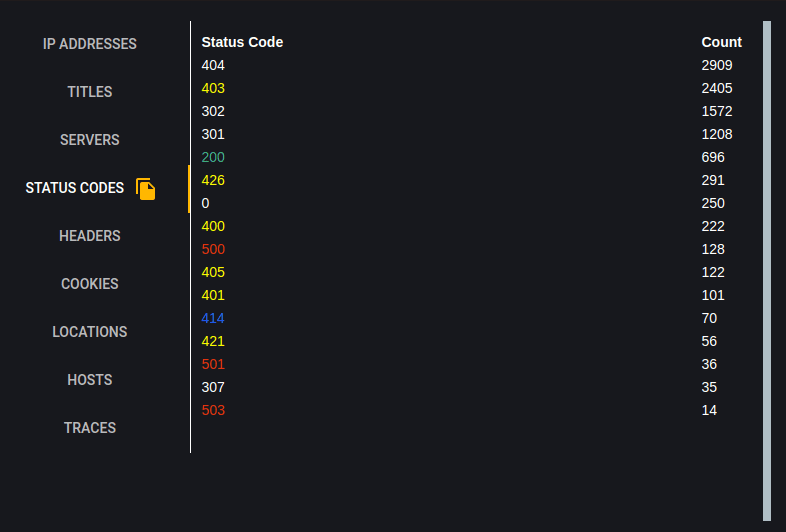
Headers
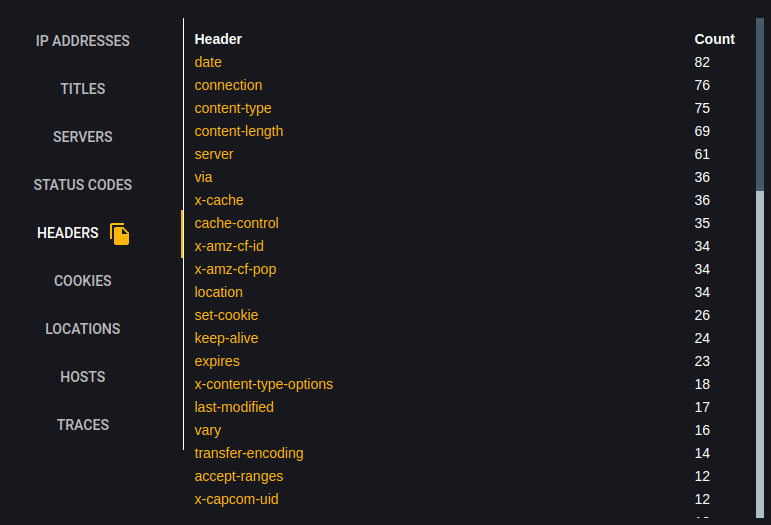
Cookies
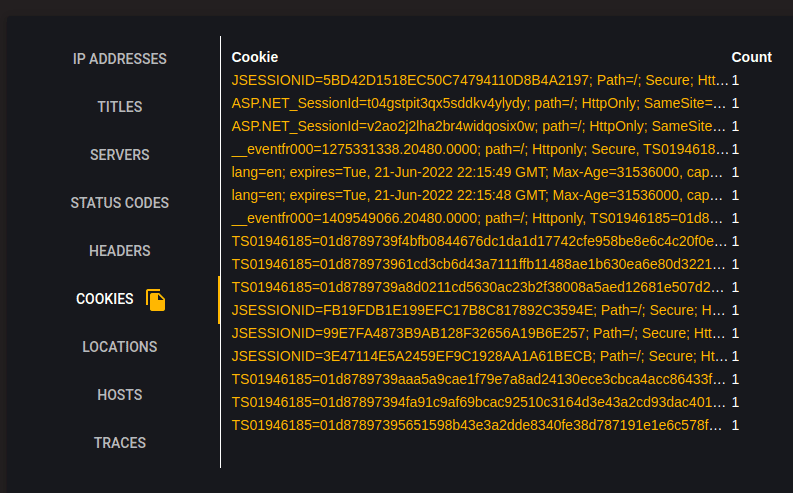
Locations
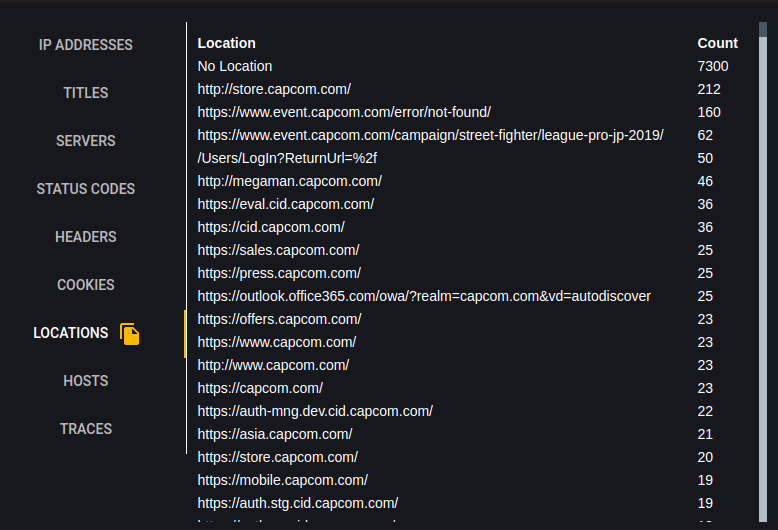
Hosts
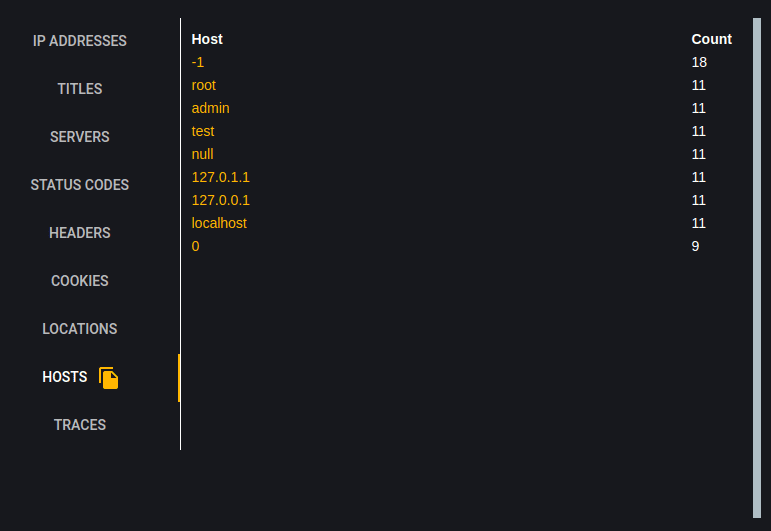
Viewing 'Subdomain Results'
F. You can view all subdomains that returned results by clicking on the domain name in the upper-left of the Report view. Once clicked, you will be redirected to the query results view.
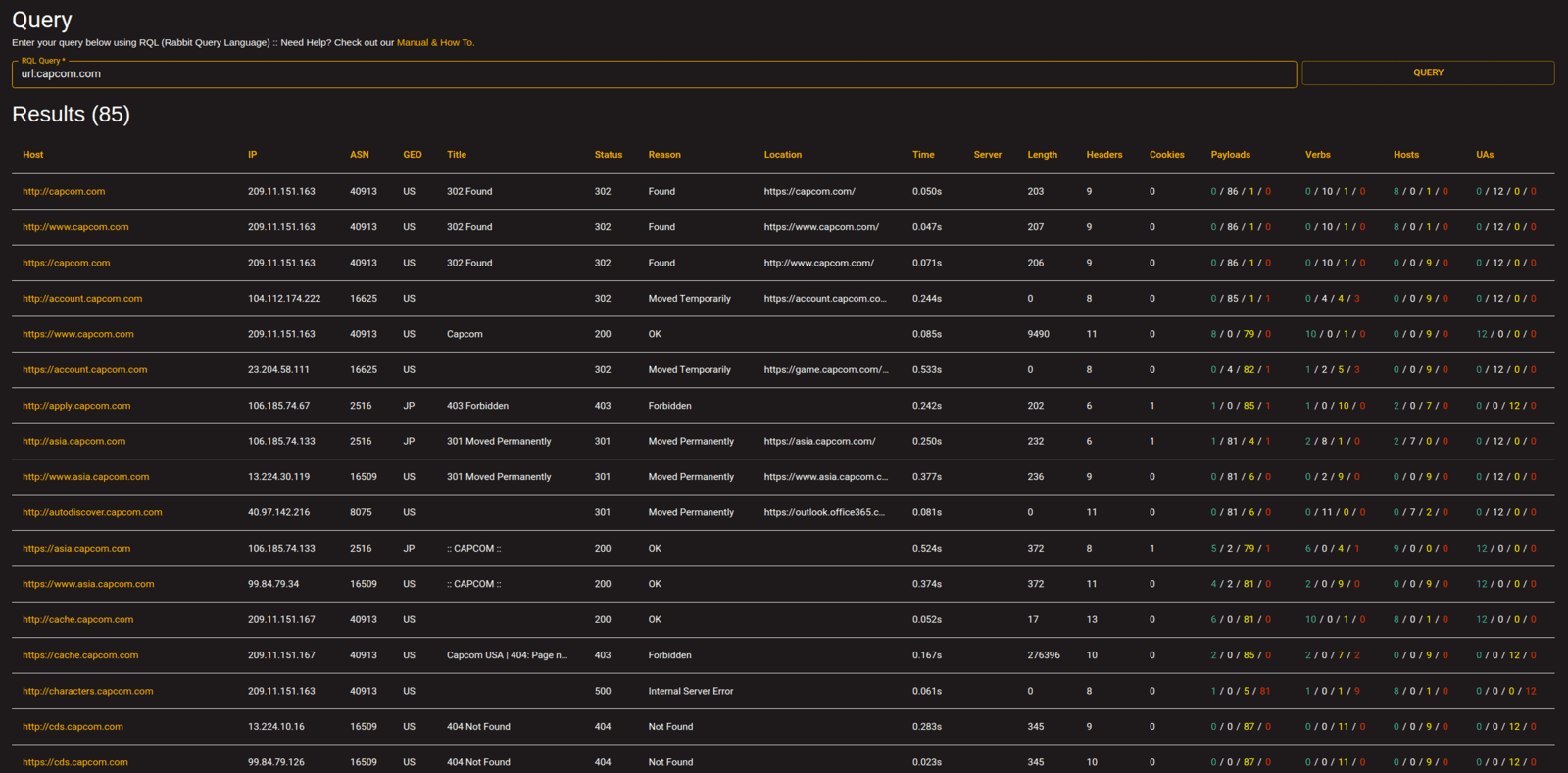
G. This view is similar to normal spreadsheet (.csv) output, with columns and rows of result data (with each discovered subdomain/host on a new line or row). From this view you can click on the desired Subdomain/Host to drill into the Subdomain View. Detailed descriptions of column data below:
| Host | Subdomain or hostname |
|---|---|
| IP | IP address of host |
| ASN | ASN ID |
| GEO | Geography or Region |
| Title | Title of default webpage of default container of host |
| Status | HTTP response status code |
| Reason | Reason why status code was provided |
| Location | Landing page of 301/302 redirect |
| Time | Total time in seconds the request to complete |
| Server | Serer name header value |
| Length | Content-length of request body |
| Headers | Total numbers of observed headers in response |
| Cookies | Total numbers of observed cookies in response |
| Payloads | 100+ payload status code result totals - 2xx=Green, 3xx=Yellow, 4xx=White, 5xx=Red |
| Verbs | 11 verb enums status code result totals - 2xx=Green, 3xx=Yellow, 4xx=White, 5xx=Red |
| Host Header | 9 host header status code result totals - 2xx=Green, 3xx=Yellow, 4xx=White, 5xx=Red |
| UAs | 12 user-agent status code result totals - 2xx=Green, 3xx=Yellow, 4xx=White, 5xx=Red |
2D. Viewing the Results - Subdomain View Explained
A. Once you click on a specific host or subdomain you will be presented with the Subdomain View. This view will provide information about all crawls performed on the subdomain and associated response data.
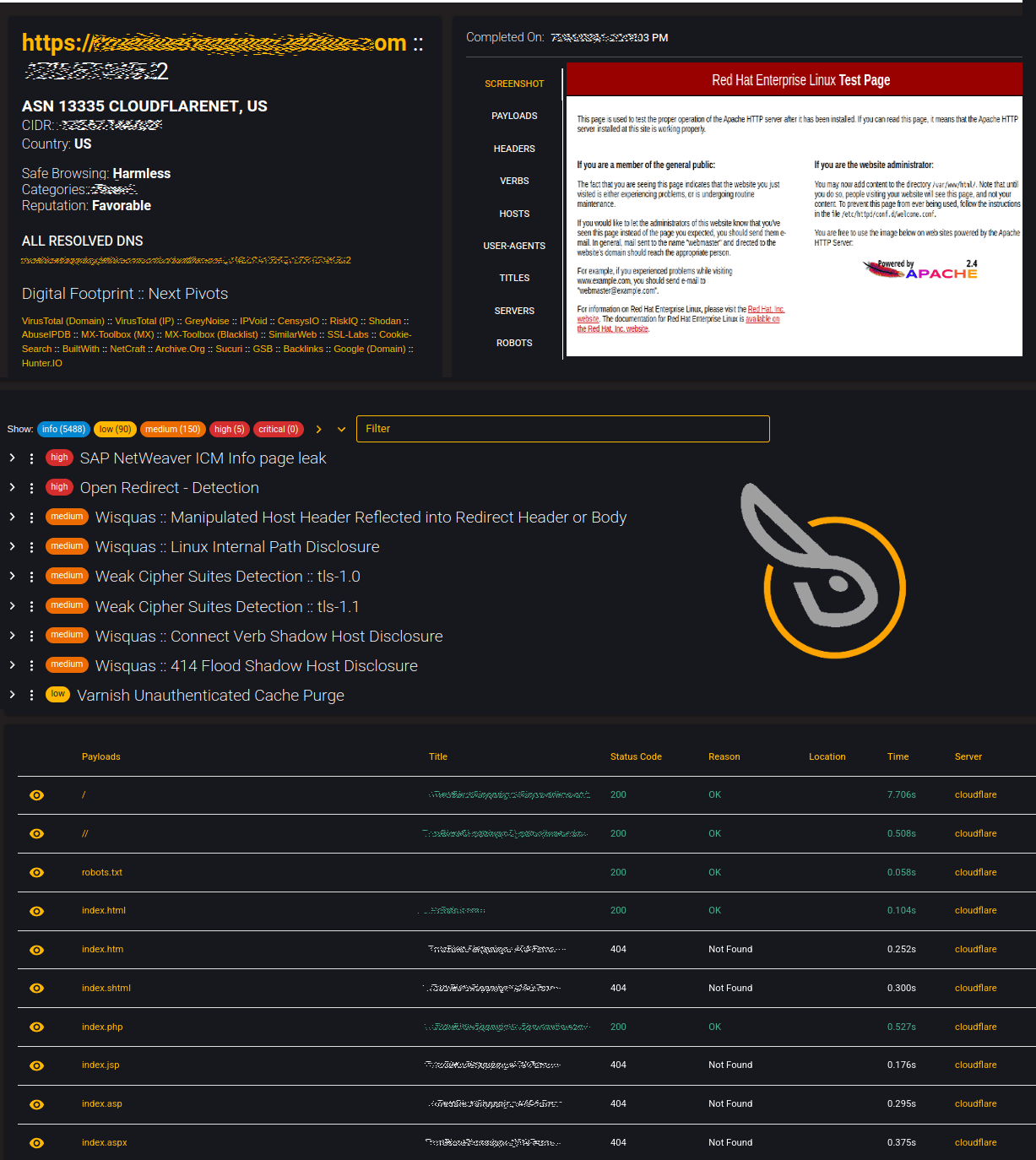
Domain/IP/ASN/DNS Information
Subdomain & Scanned IP/Host
ASN / GEO Information
Reputation Lookups / Blocklists
All Resolved DNS (click on host for ASN Info)
OSINT / Social Media / Attribution / Framework
Data Leakage Awareness / Google Dork Links

Scoreboxes - Total Results for Subdomain Requests
Payloads - 100+ payload results
Headers - All observed headers
Verbs - HTTP Verb enumeration results
Hosts - Host header results
User-Agents - All unique User-Agent header values
Titles - All unique Title header values
Servers - All unique Server header values
Robots - Output of robots.txt file if it exists
414Flood - Output of leaked shadow vhosts if exists
Headers - All observed headers
Verbs - HTTP Verb enumeration results
Hosts - Host header results
User-Agents - All unique User-Agent header values
Titles - All unique Title header values
Servers - All unique Server header values
Robots - Output of robots.txt file if it exists
414Flood - Output of leaked shadow vhosts if exists
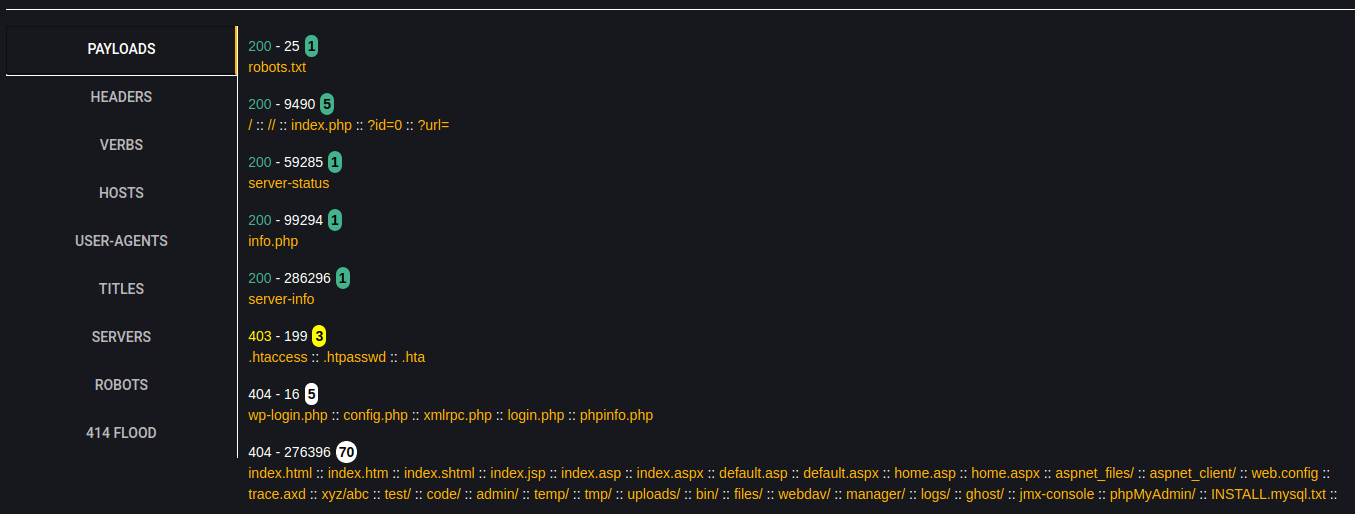
Payload Results Listing with Response Information
B. This view is similar to normal spreadsheet (.csv) output, with columns and rows of result data (with each payload result on a new line or row). Detailed descriptions of column data below:
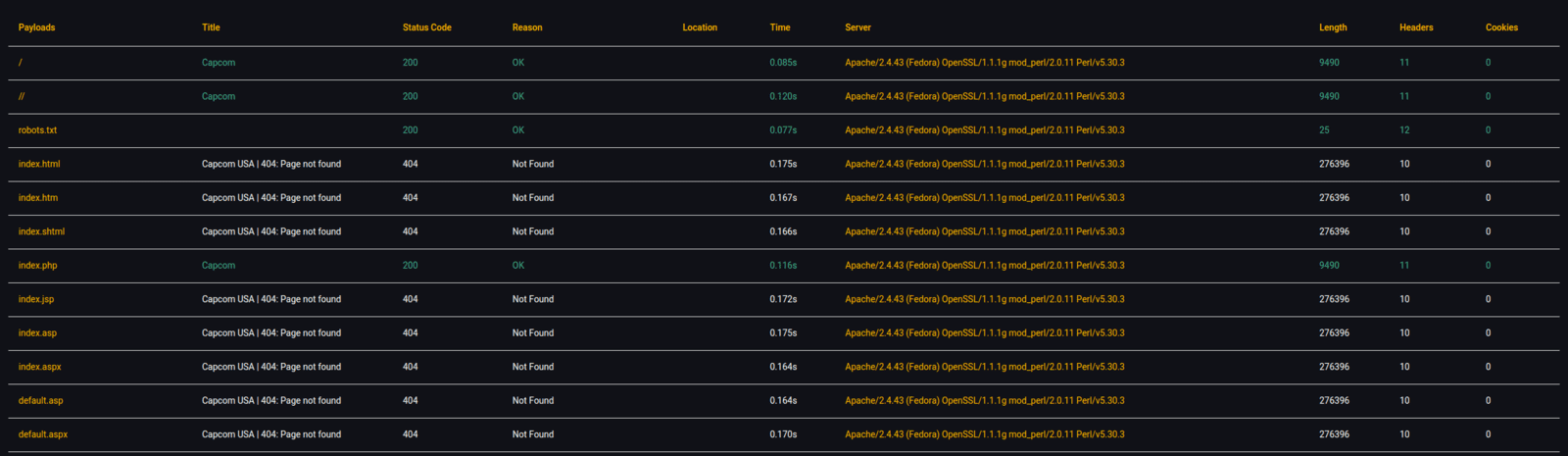
| Payload | Payload string or content requested from web server |
|---|---|
| Title | Title of webpage of requested payload |
| Status Code | HTTP response status code |
| Reason | Reason why status code was provided |
| Location | Landing page of 301/302 redirect |
| Time | Total time in seconds the request took to complete |
| Server | Server name header value |
| Length | Content-length of request body |
| Headers | Total numbers of observed headers in response |
| Cookies | Total numbers of observed cookies in response |
C. Clicking on Payload name (ie: index.html) will open a browser request to that specific URL. Clicking on 'Server' will result in a lookup on https://cve.mitre.org/ for web server vulnerabilities.
Payload Results Listing with Response Information
D. You can validate results by clicking on the 'COPY ICON' to copy the custom curl command to your clipboard.
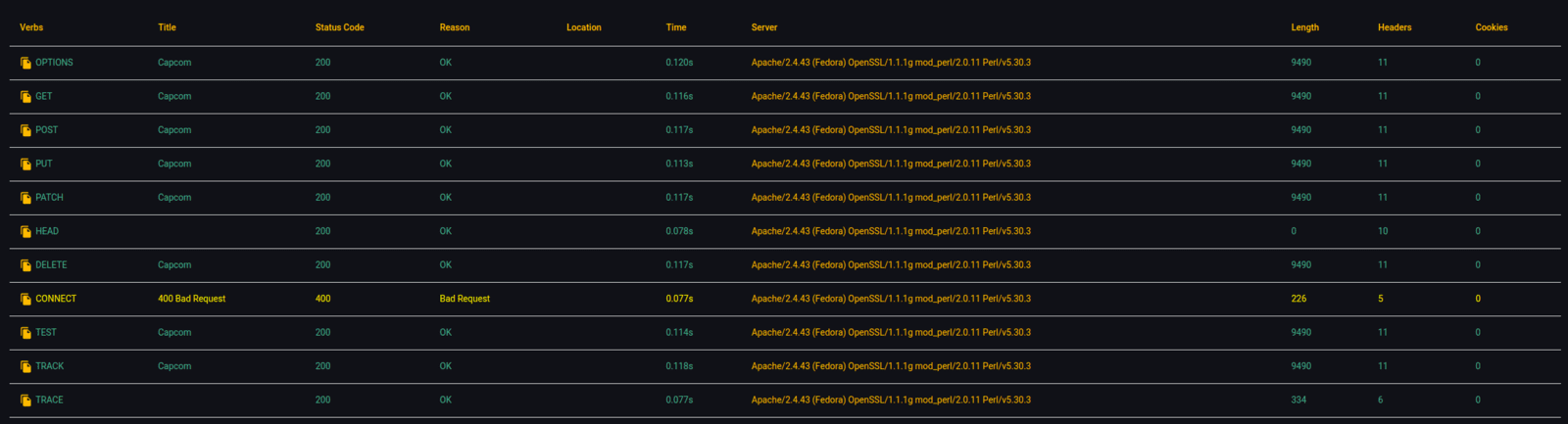
Payload Results Listing with Response Information
E. You can validate results by clicking on the 'COPY ICON' to copy the custom curl command to your clipboard.
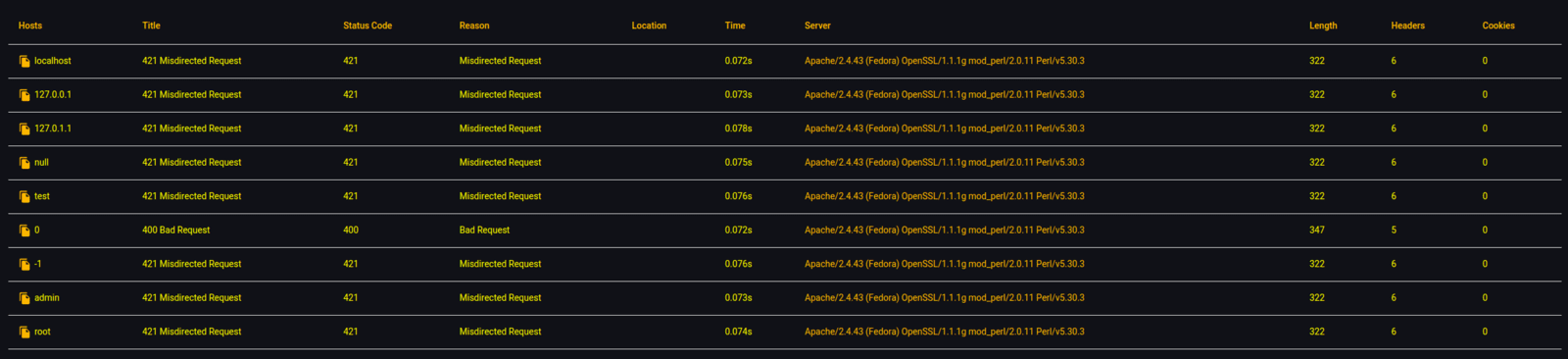
Payload Results Listing with Response Information
F. You can validate results by clicking on the 'COPY ICON' to copy the custom curl command to your clipboard.
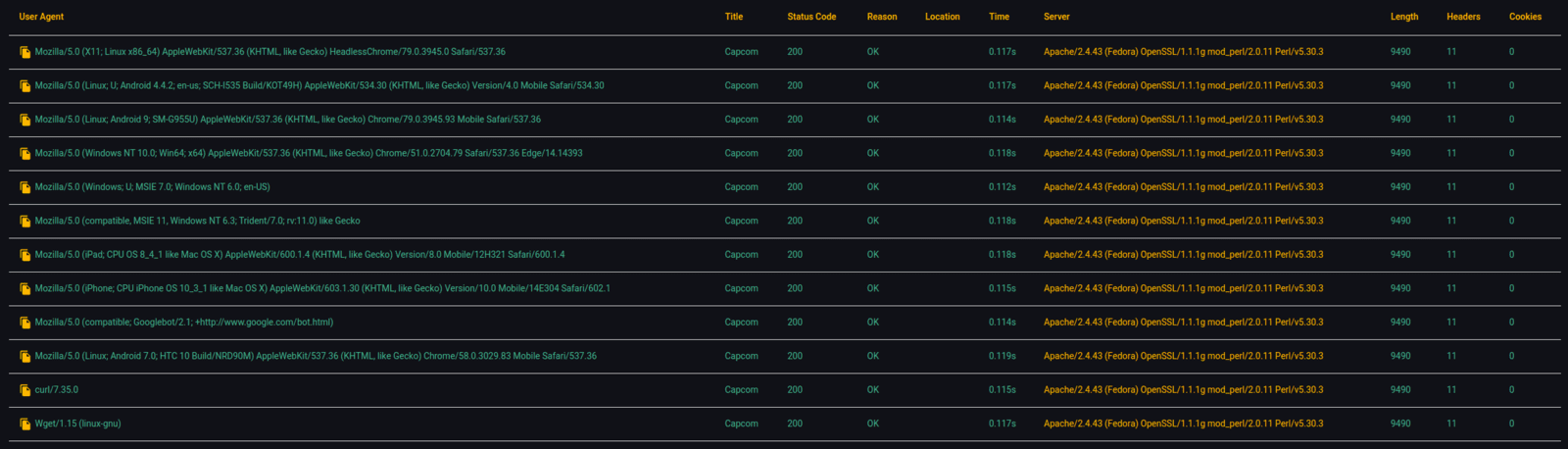
2E. Searching - Domain vs. Global
A. Through crawling efforts and storing some results with WisQuas, Lost Rabbit Labs is building a haystack of digital inventory for further analysis. Once all crawls have completed you can search all saved data using our custom Rabbit Query Language (RQL). RQL is Lucene based, with some additional custom search parameters and scoring methods (more info below) to increase likelihood of retrieving legitimate findings versus false positive findings. Our goal is to decrease noise-to-signal ratio, and increase the amount of actionable intelligence provided by WisQuas.
RQL Parameters Defined
Example WisQuas Searches Using RQL
NOTE: You must start your query with one (1) of the following before using other parameters: url, payload, verb, host, header, header.headername
Find all subdomains for a domain:
url:domain.tld
Find a unique host:
url:www.domain.tld
Find results in entire database where title matches "Index of /":
url:. title:"Index of /"
Find all instances of 'phpMyAdmin' in entire database:
url:. payload:phpMyAdmin/ title:"phpMyAdmin"
Find successful hidden container or Shadow VHOST access:
host:. status:200 baseline.status:!200
Some Lucense is supported including wildcard (.) and fuzzy matching ($).
payload:server-status url:. title:$"Apache Stat" status:200 length:55,9999999
2F. OSINT & 'Next Pivots' - Digital Footprinting / Threat Intel

On some views you will be presented with Whois Information, Digital Footprint & Next Pivots, along with OSINT and informational links to external sites. Click on the 'Next Pivots', which include the Whois attributes (orgname, person, emails, IP address) and you will be shown a list of domains associated with that attribute.
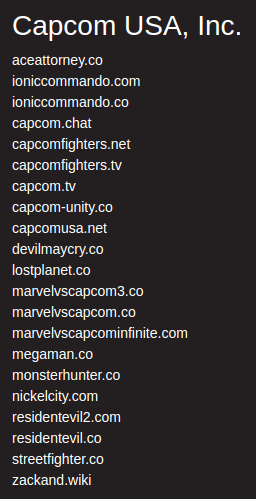
3. Feedback
We appreciate your interest in WisQuas and would love to hear your feedback or new feature requests. You can submit your feedback using the link below:



