HTTP/HTTPS Header Analyzer
During Web Application & API Penetration Testing engagements there is always a need to evaluate headers and cookies of given endpoints in order to ensure security requirements are being met. Currently, many of the existing open-source tools for header analysis seem to be outdated, missing newer headers, inconsistent with results, and thus lacking proper detections. With this as the inspiration, our team set out to create an open-source solution to make analyzing headers easier for both Offensive and Defensive security teams.
GimmeHead3rz is a HTTP/HTTPS header analyzer created to help quickly identify and audit discovered headers for any given endpoint against known common/security header lists. These custom lists contain commonly found headers, along with Best-Practice security headers, that are customizable for specific needs. GimmeHead3rz will report back on all discovered common, anomalous, and security headers based on these lists, and will provide results around missing security headers and associated security flags.
GimmeHead3rz supports the following functionality:
- Single target and bulk URL analysis
- Customizable Hostname, HTTP Headers, VERBs, Cookies, and User-Agents
- Ignore bad certificates on HTTPS requests (through the --insecure flag)
- Follow redirects on all requests (through the --redirects flag)
- Authenticated analysis using custom Headers and/or Cookies
- Customizable common-headers.txt and security-headers.txt files for different use-cases
Installation instructions can be found here. Using GimmeHead3rz on a single target is as easy as:
./gimmiehead3rz.py http://www.example.com
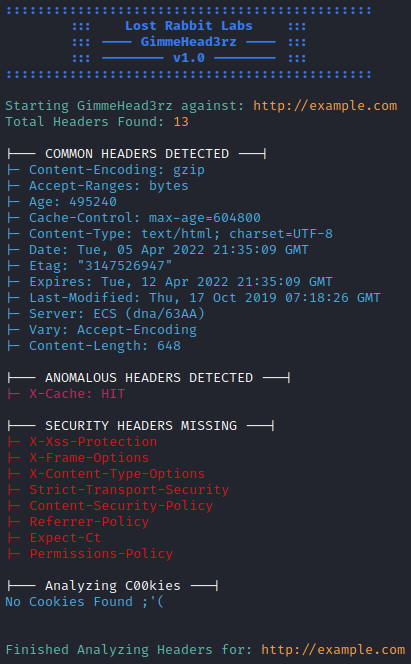
Results are color coded and grouped by category for convenience. Advanced functionality includes modifying HTTP headers, cookies, verbs, user-agents, using a target file for bulk lookups, and more (examples below).
Perform scan on all URLs in ‘targets.txt’ file:
./gimmehead3rz.py -t targets.txt
Authenticated scan with custom cookie and header:
./gimmehead3rz.py https://example.com -h “name:value” -ch “name:value”
Ignore cert errors with custom timeout (25 seconds):
./gimmehead3rz.py http://example.com -i -to 25
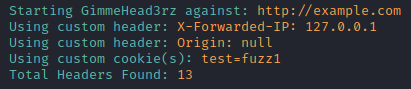
Using custom header and cookie to create request authentication:
./gimmehead3rz.py http://example.com -ch "X-Forwarded-IP:127.0.0.1" "Origin:null" -c "test:fuzz1"
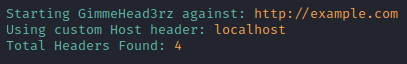
Using custom host header to scan hidden localhost web container:
./gimmehead3rz.py http://example.com -host localhost
Let us know what you think of of GimmeHead3rz (contact us), and help us make it better by contributing to the project (https://gitlab.com/lost-rabbit-labs/gimmehead3rz). For more information visit our readme here.



